IEC 61850 interoperability with IEC 104
IEC 61850 Server
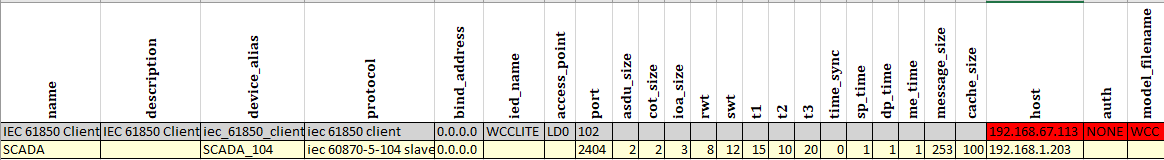
WCC Lite can act as a IEC 61850 server to serve data to remote SCADA systems. For example, WCC Lite can be used to acquire data from various protocols (Modbus, IEC 60870-5-103, etc.), this data can be redirected and propagated further to a single or multiple IEC 61850 clients. IEC 61850 Server supports TCP and TLS connection types. TCP connection can be secured with password authentication.
Commands
WCC Lite IEC 61850 Server implementation defines four command types which are described by their control model:
- Case 1: Direct control with normal security (direct-operate);
- Case 2: SBO control with normal security (operate-once or operate-many);
- Case 3: Direct control with enhanced security (direct-operate);
- Case 4: SBO control with enhanced security (operate-once or operate-many).
Normal security commands are considered for execution if the command signal is found in Excel configuration. There aren’t any additional checks in command execution in any master protocol.
Enhanced security commands need feedback from master protocol to either to succeed or fail. If feedback is not received within command_ack_timeout_ms timeframe, the command is considered as failed.
Command value attributes (e.g. stVal) must be updated separately (if they need to be updated).
When using SBO commands, select is not routed to master protocol and select logic is performed only in IEC 61850 Server protocol.
IEC 61850 Client
WCC Lite supports IEC 61850 Client command functionality that is used to control server devices such as protection relays. As relays require fast, secure and responsive interfaces, WCC Lite can be considered as a valid option.
Supported commands
Currently WCC Lite supports three types of commands:
-
setVal command;
-
setMag.f command;
-
Oper.ctlVal commad.
If configured all commands will be added to excel using WCC-Utility.
How commands function
|
ctlModel |
Description |
|---|---|
|
|
Signal cannot be controlled |
|
|
Direct execution of a command |
|
|
Command is selected and then executed |
|
|
Direct execution with a force wait of command termination |
|
|
Command is selected and then executed; waiting for command termination |
If ctlModel is status-only, messages via Redis will be ignored for this point, otherwise a Redis subscribe callback will be launched to handle commands as soon as they are sent over Redis. If CDC of a signal does not have means of control, ctlModel parameter is ignored.
Controlling remote equipment via commands
The control model provides a specific way to change the state of internal and external processes by a client. The control model can only be applied to data object instances of a controllable Common Data Class (CDC) and whose ctlModel DataAttribute is not set to status-only. Such data objects can be referred to as control objects. If controls are enabled in a IEC 61850 Server device the user can configure controls by filling control_model column in Excel configuration with a control model direct-with-normal-security, sbo-with-normal-security, direct-with-enhanced-security and sbo-with-enhanced-security as well as setting functional constraint in da_fc column to CO.
Command “direct-with-normal-security”
As the IEC 61850 protocol states direct-with-normal-security command simply executes a command directly without any additional selection or execution logic. This is the most basic use of commands. Does not contain any command termination logic.
Provided below is command direct-with-normal-security standard logic of successful command and failed command:
Successful command logic
Failed command logic
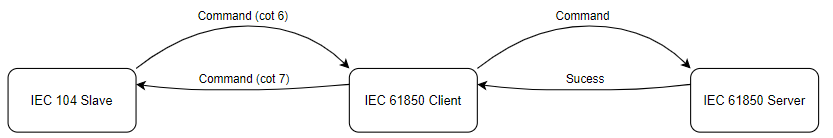
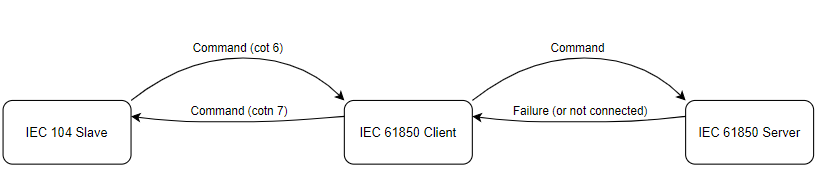
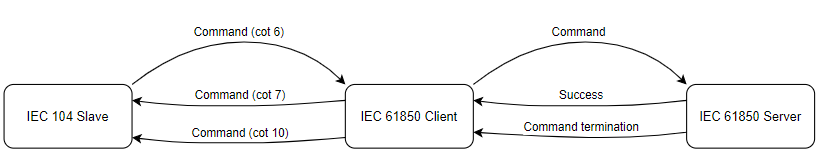
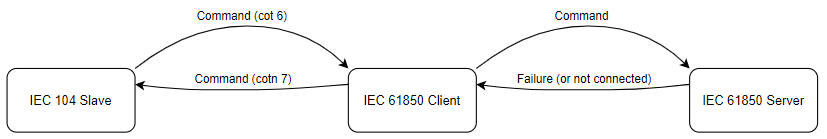
Command “sbo-with-normal-security”
As the IEC 61850 protocol states sbo-with-normal-security command uses select and execute command logic. First, the command is selected, and then the execute command is sent to the server. Does not contain any command termination logic.
Provided below is command sbo-with-normal-security standard success and failure logic:
Successful command logic
Failed command logic
Regarding failure, if server fails to select cotn 7 is returned the same way if an execute fails.
Command “direct-with-enhanced-security”
As the IEC 61850 protocol states direct-with-enhanced-security command uses execute command logic. Contain command termination. This means that command awaits for termination message. The execute command is sent to the server, and the command waits for a termination message from the server. If the termination message is received, the command is considered successful, and if not, the command is considered failed.
Provided below is command direct-with-enhanced-security standard success and failure logic:
Successful command logic
Failed command logic
In case of failure, no command termination is additionally provided.
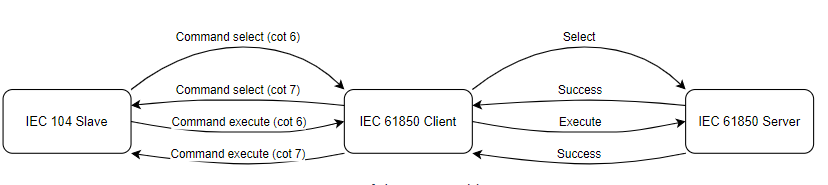
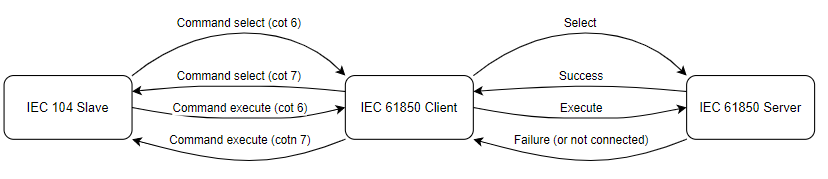
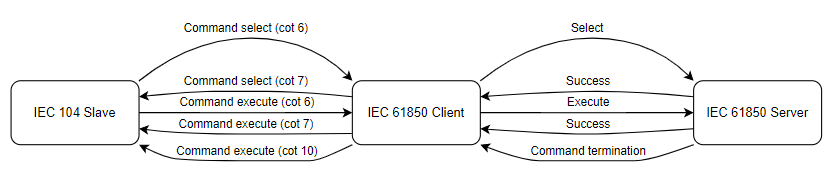
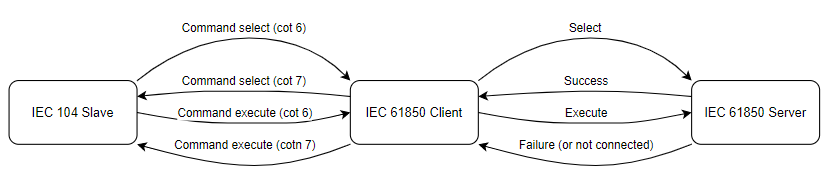
Command “sbo-with-enhanced-security”
As the IEC 61850 protocol states sbo-with-normal-security command uses select and execute command logic. Contains command termination. This command is similar to the sbo-with-normal-security command, but it also responds with a termination message. If the command is successful, the termination message is sent to the client, and if not, the cotn 7 is returned.
Provided below is command sbo-with-enhanced-security standard success and failure logic:
Successful command logic
Failed command logic
In the case of failure, sbo command acts the same way as direct command. It does not send command termination, only cotn 7.
Basic protocol functionality
The server (controlled station) delivers various data to the client.
• Data object values reported upon changes
• Data object values reported cyclically
• Responses to control commands
• Responses to read requests
To enable interoperability between IEC 61850 and IEC 60870-5-104, mapping between the two protocols is necessary. This mapping involves defining which data objects from one protocol correspond to which data objects in the other protocol.
Excel configuration Devices sheet
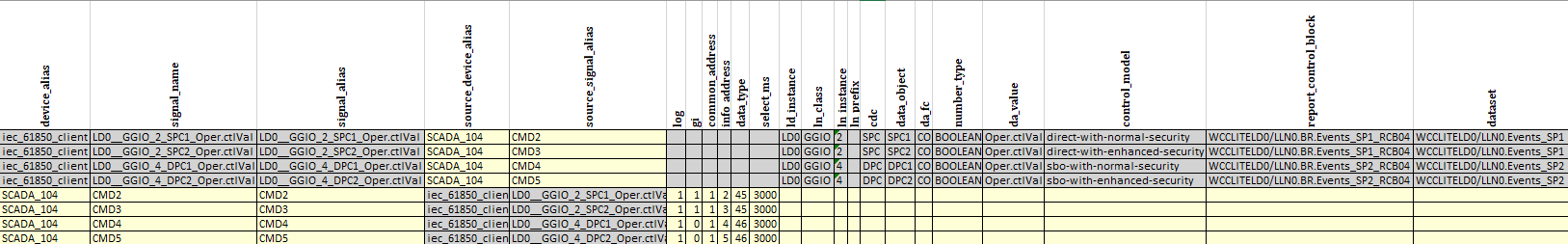
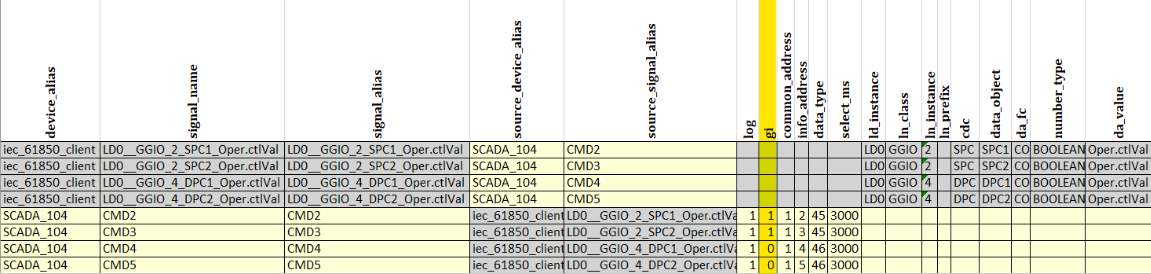
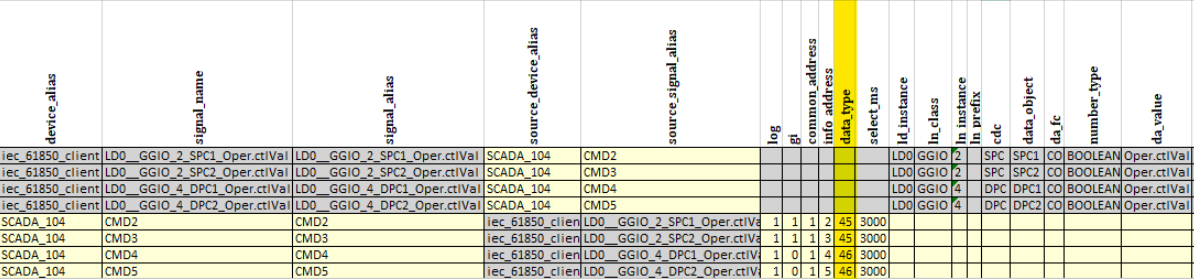
Excel configuration Signals sheet
The client can at any time request the present process data values by issuing interrogation commands. The command may be a general interrogation (GI) request, where all data objects with GI indication configured “1” are reported.
Signals sheet
IEC 60870-5-104 data objects
Single-point information
Single-point information is derived from several IEC 61850 boolean data attributes
• SPS.stVal
• SPC.stVal
| Type | ASDU | ||
| GI | 1 | M_SP_NA_1 | Single point |
| Event | 30 | M_SP_TB_1 | Single point with CP56Time2a |
Single-point information
Double-point information
Double-point information is derived from several IEC 61850 data attributes.
• DPS.stVal
• DPC.stVal
| Type | ASDU | ||
| GI | 3 | M_DP_NA_1 | Double point |
| Event | 31 | M_DP_TB_1 | Double point with CP56Time2a |
Double-point information
Control operations
Single command
Single-command controls are performed towards SPC (controllable single point) IEC 61850 target objects. The command can be given with or without a time stamp (C_SC_NA_1, C_SC_TA_1). Only direct type operations are allowed.
Single command
Single-command control operations can be performed towards SPC (controllable single point) data class objects. Only direct controls are allowed.
• SPC.Oper.ctlVal
| Type | ASDU | ||
| Control | 45 | C_SC_NA_1 | Single command |
| Control | 58 | C_SC_TA_1 | Single command with CP56Time2a |
Single command
Double command
Double-command controls are performed towards DPC (controllable double point) IEC 61850 target objects, that is, circuit breakers and controllable disconnector objects. The command can be given with or without a time stamp (C_DC_NA_1, C_DC_TA_1). If time tagged commands are used, it is important to ensure the master and the relay times are synchronized.
Each double-point DPC object has two predefined IEC 60870-5-104 control objects: one intended for direct operation and the other one for select-execute (select-before-operate) operation.
Double command
Double-command control operations can be performed towards DPC (controllable double point) data class objects. Direct controls are always possible. Two-step select-execute controls are also possible if the target DPC object allows it. There are two different control objects available for the direct and select-execute alternatives.
• DPC.Oper.ctlVal
| Type | ASDU | ||
| Control | 46 | C_DC_NA_1 | Double command |
| Control | 59 | C_DC_TA_1 | Double command with CP56Time2a |
Double command
Direct operation
Direct operation is always possible for the double command regardless of the control model (direct or SBO) configured for the target IEC 61850 DPC object. If the control model is SBO, the IEC 60870-5-104 stack automatically performs the two needed operations (select and operate) towards the DPC object.
Select-execute operation
A two-step select-and-execute operation is possible only if the target DPC object’s control model is configured as select-before-operate (SBO). For most target DPC objects, the default control model setting mode is SBO. IEC 60870-5-104 selection timeout is defined by the protocol instance’s Selection Timeout setting parameter. When a command is performed from the IEC 60870-5-104 instance, the selection timeout setting configured for the IEC 61850 DPC target object is overridden. Cause of transmission and selected status The relay’s native IEC 61850 data model does not include any cause of transmission (COT) information data. Therefore, monitoring object transmissions from the IEC 60870-5-104 stack can only include the following cause of transmission values.
• 1 = Cyclical
• 3 = Spontaneous
• 20 = General interrogation
• 21...36 = Group 1...16 interrogation
The control command’s response message returned to the controlling client includes COT value 11 = Remote command, but the controlled object value change in monitoring direction is always COT=3 (Spontaneous). While this information is not so important for the controlling client, it can be for another client in a multiple-client environment.